Expert IT Blog
Featured Article
VLOG: Detecting Cyber Attacks in a Flash: Introducing IBM FlashCore Modules Gen4
4:00 Detecting Cyber Attacks in a Flash:Introducing IBM FlashCore Modules Gen4 Cyber threats are becoming increasingly sophisticated, leaving organizations highly challenged to safeguard their valuable data assets. IBM’s addition of the new AI-enhanced versions of the...
Recent Articles
BLOG: Selecting the Right PowerEdge Server for SMB and Midrange Businesses
Bryan Samson Strategic Alliances Manager Today’s small and medium businesses need flexible and cost-efficient server platforms to support their application and overall business growth needs. They also need to keep human resource expenses in check and tend to...
BLOG: Dell EMC PowerStore Exhibits Strong Market Acceptance and Growth
Bryan Samson Strategic Alliances Manager Dell Technology’s PowerStore has seen a doubling of orders from the May 2020 launch through October 2020 (Dell’s Q3). And in its first three quarters, PowerStore is ahead of XtremIO and VxRail in their equivalent...
BLOG: IBM Power Systems Latest Software Updates
Ron Gordon Director » Power Systems Recently, IBM released updates to almost all the system software supporting Power Systems. These updates apply to and support almost all data centers, adding efficiencies and automation. At last year’s Virtual Power Technical...
BLOG: Benefits of VMware Software Subscription Enterprise License Agreement
Bryan Samson Strategic Alliances Manager “But it’s only $5.99 per month,” my daughter says regarding a new streaming service. In contrast, basic cable monthly contracts cost about $50-$100 per month, so it sounds like a good deal. But let’s add up the...
BLOG: IBM FlashSystem 5200 Entry-Level Storage Unveiling
Keith Thuerk Storage Engineer On February 9, 2021, IBM announced a new, rejuvenated FlashSystem array, the FlashSystem 5200, boasting superior application performance and an increase in ROI. The new FlashSystem 5200 (FS5200), intended to replace the IBM...
BLOG: Unstructured Data Solutions (UDS) – Dell Technologies
Bryan Samson Strategic Alliances Manager Unstructured data or non-database data like loose files, PDFs, photos, and video clips represent nearly 90% of annual data production with a growth rate of 55-65% each year, according to Forbes. That is an explosive...
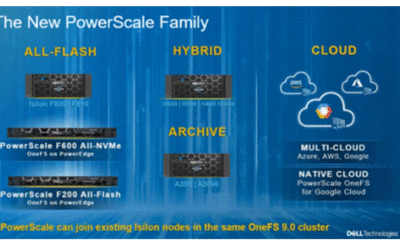
BLOG: Dell EMC PowerScale Review: Enterprise Storage Solution for Object, Block, and File
Keith Thuerk Storage Engineer Modern data centers are built around several innovative IT building blocks, such as flexibility, agility, automation, and security. What does that really involve from a technology standpoint? Examples include an updated network...
VLOG: Cisco Security
4:54 Cisco’s rebranding of their security portfolio has been a game changer. Unified with the Cisco SecureX dashboard, the Cisco cybersecurity portfolio provides an efficient, solid security platform for IT professionals. Video Highlights Secure Firewall...
BLOG: Dell EMC PowerStore Metro Node Automates Business Continuity
Bryan Samson Strategic Alliances Manager Dell’s Midrange Storage flagship with industry-leading sync technology. This is a game changer for IT departments, since making data consistently available to your constituents is a constant struggle. As business needs evolve...
VLOG: Riverbed Solutions for the Cloud Era
4:20 Riverbed Solutions for the Cloud Era Video Highlights Overcome Cloud Traffic Latency Issues Improve Performance for Remote Workers Optimize Cloud Traffic with Riverbed Cloud Accelerator Increase Performance and Agility for SaaS Apps with Riverbed SaaS...
BLOG: Cisco Email Security Solutions
Marie Ashway Director of Marketing Email security breaches continue to be the number one threat vector both at work and in our personal email activities. Email also just happens to be one of the most important tools individuals and companies use to...
BLOG: Dell EMC PowerProtect DD: A Cloud-Enabled Solution
Keith Thuerk Storage Engineer Dell EMC PowerProtect DD is now setting the bar for data management from edge to core to cloud, giving you everything you need to protect a modern data center. PowerProtect DD is labeled as cloud-enabled, but what exactly does that...