Systems Engineer
Since its initial release in 2004 (that seems longer ago than it probably should), the IBM DS8000 series has been the flagship of the IBM Storage product line.
Although it is commonly seen as a mainframe or z/OS storage system, and it does have the ability to provide CKD volumes over FICON, it has always also been capable of presenting Fixed Block storage to open systems environments that required its combination of high availability, advanced copy services, and performance.
The DS8900F family has been no exception and the systems are found in many high-performance AIX, Linux (whether Red Hat or Suse), and IBM i environments along with the traditional mainframe systems.
As has been the case with earlier releases of the DS8000, the DS8900 is seeing a major new announcement with microcode release 9.2 (as of July 20th). This release can be divided into two parts: 1) A new addition to the DS8900F family, and 2) enhancements to the microcode functions. We will start with the former.
The DS8980F “Analytics Class”
Those who have been around the DS8k for a while will remember that the DS8880 family of storage solutions, with the release of All Flash systems, introduced the DS8888F “Analytics Class” system. This system was designed to address applications with the highest requirements for response time and availability, but without moving data from Flash Tiers to spinners of either Enterprise Class or Nearline Class. It had the highest core count of any member of that family of systems and was really focused on making the DS8000 a solid platform for doing everything in Machine Learning (ML) and Artificial Intelligence (AI).
At launch, the DS8900F family product line was more limited than the DS8880 family. Beyond no longer having hybrid systems, the systems available were the DS8910F models, with a customer rack mounted and a model that came with its own IBM rack, designed for smaller environments and the “Agility Class” DS8950F model, the workhorse of the family, with up to 20-cores and 2 TB of cache.
IBM has introduced a new DS8900F model “Analytics Class” system. The DS8980F model builds on the DS8950F model and then blows it away. The number of CPU cores (still based on the IBM power systems Power 9 processor) jumps to 44 cores in this new system. The cache also makes a huge jump from 2TB to 4.3 TB.
Another advantage of the newly designed system is the increase of the already highly available nature of the DS8000. With the DS8980F, the uptime increases to 99.99999% (compared to merely 99.9999% availability on the DS8888F).
As with previous generations of DS8000, you can expect that the warranty will be from 1 to 4 years, depending on the Machine Type
Performance
As you can probably surmise, the DS8980F screams. Looking at the DS8888F as a basis of comparison, you can see in the graph below that a reduction of 18-25% latency is easily accomplished with the DS8980F. It is possible that performance gains would be larger when compared to other systems.
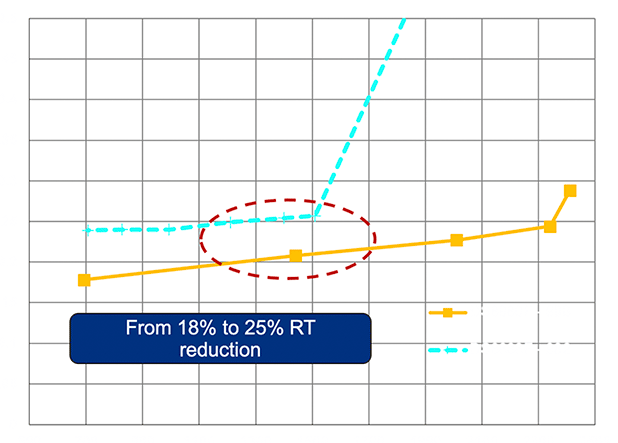
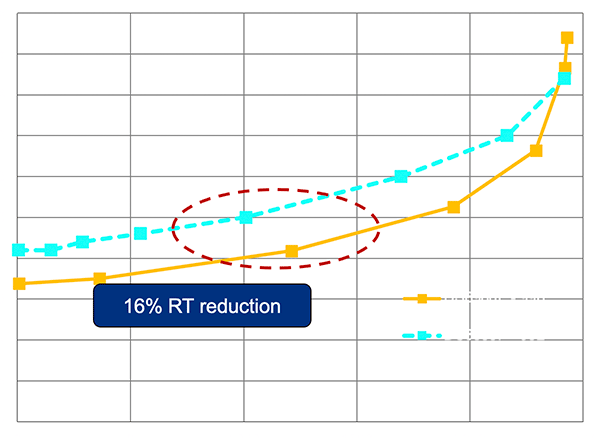
Code improvements
Not everything in this announcement is specifically about the DS8980F, though. Any member of the DS8900F family will be able to update to the R 9.2 version of the microcode, and the improvements address a wide range of issues. I’ll address some of the more eye-catching ones, but please talk to your Mainline Storage SE for all of the details.
- Data protection
The problems stemming from malware and malicious hackers are well known to the IT industry. It was not long ago that, in the United States, we experienced a large jump in gasoline prices because of the Colonial Pipeline attack. This trend has spread to all sorts of industries, and protecting the data from these attacks is a real priority.
With the DS8880 family, IBM already had the SafeGuarded Copy (SGC) capability. It is, in some ways, similar to IBM System Storage FlashCopy, in that it creates a point in time copy to recover from in the event of some sort of malicious attack. Where it differs is that it is controlled by either GDPS or Copy Services Manager (CSM) and allows users to create air-gapped and immutable copies of data. These copies, unlike FlashCopy, cannot be mounted to any host. The copies can be used to recover quickly in the event of an attack which encrypts the production data by first copying them to a Recovery Volume. (Of note, I attended a presentation by a security vendor at the last in-person IBM Systems Technical University and it was interesting hearing how a malicious attack in a mainframe environment could potentially turn its cryptographic processors against the data.)
Some customers will try to use backup for this, but, because malicious hackers may leave their code for some time before turning it on, it can be difficult to find a version of the backup that is not corrupted. By using SafeGuarded Copy, it is possible to have numerous copies of the data on disk, and when systems are restored, the data is still there for forensic analysis by the three-letter acronym of your choice, in terms of determining who was responsible. This makes it much easier to recover from a malicious attack with a lower RPO than would typically be expected.
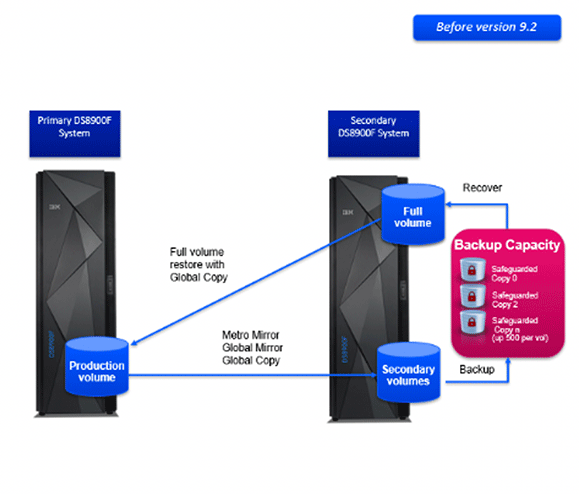
Obviously, full volume copies take a significant amount of time and bandwidth. This is a less than desirable situation when the production data has already been corrupted or encrypted and you need to recover quickly.
With Release 9.2, this problem is solved. A recovery volume for the SGC Copy can replicate only those tracks that are needed to restore the production volume back to the desired state, potentially changing the copy time from hours to seconds.
Additionally, the SafeGuarded Copies will be created faster, only holding the Global Mirror link for around 30 seconds while the copy is made.
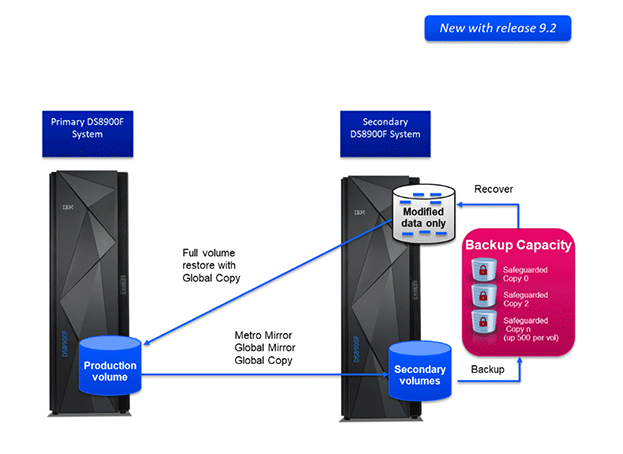
Obviously, full volume copies take a significant amount of time and bandwidth. This is a less than desirable situation when the production data has already been corrupted or encrypted and you need to recover quickly.
With Release 9.2, this problem is solved. A recovery volume for the SGC Copy can replicate only those tracks that are needed to restore the production volume back to the desired state, potentially changing the copy time from hours to seconds.
Additionally, the SafeGuarded Copies will be created faster, only holding the Global Mirror link for around 30 seconds while the copy is made.
IBM z “Cyber Vault” enhancements to Safeguarded Copy
SGC is a powerful technology, but it isn’t a complete solution. SGC allows you to have numerous iterations of copies, air-gapped and secure. But when will you notice the problem that requires a restore from one of the SGC iterations? How do you know which copies of data are safe to access?
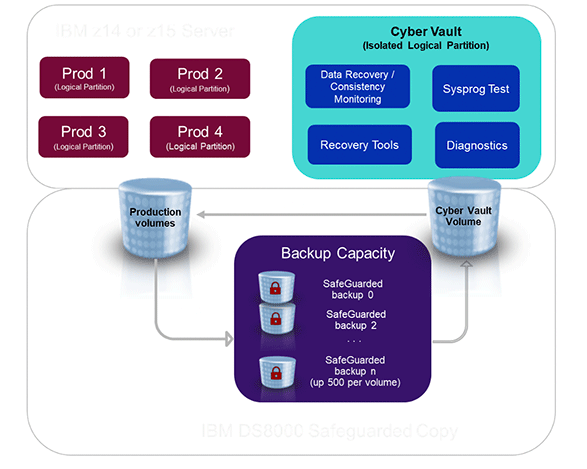
It is worth noting that IBM z Cyber Vault is managing the intelligence part of protection against malicious attacks and logical corruption. It still relies on Copy Services Manager (CSM) or GDPS to create and manage the SafeGuarded Copy process. Additionally, it is restoring the SafeGuarded Backups to the Recovery volume, as you would in normal operations, to do its analysis.
Security Key Management
Data encryption continues to be a focus area for our customers. While all DS8000s, since the launch of the IBM DS8870, have been equipped with self-encrypting drives as a standard feature, not all customers take full advantage of this capability. Typically, this has been because they did not want to deal with implementing an Encryption Key Manager, such as IBM Guardium Key Lifecycle Manager.
While key managers are staying and have much to offer, with R9.2, the IBM DS8900F can now manage its own encryption keys for customers who wish to do so. Rather than setting up VMs and running multiple instances of a key manager, DS8900F users can take advantage of the Hardware Management Console (HMC) instead. Because it is standard for DS8900Fs to have two HMCs, the availability is managed.
As is already the case, Encryption is something that must be configured from the initial setup of the DS8900F. To begin using encryption on a system that is already in use you would need to fail-over to a DR system (or HyperSwap) or restore from a tape backup after wiping out the system. But for new DS8900F storage systems, this could be a great opportunity to take advantage of data encryption.
It should be noted that this capability is only for managing the keys for “Data at Rest Encryption” on the drives of the DS8900F. It will not support making encryption pervasive across your environment. If you want to do encryption in-flight, such as Transparent Cloud Tiering to an S3 bucket or IBM tape system or using IBM Fibre Channel Endpoint Security (which requires IBM z15 and the encryption-capable 32 Gbps Host Adapters on the DS8900F), an external key manager is still needed.
- Reading from Metro Mirror Secondary
As customer availability concerns have grown, and HyperSwap has matured, it has become more common to have two DS8900F storage systems, or their predecessors, in the same data center or same local area. But all IO has typically been made to the Primary Disk System.
Moreover, the fact that zHyperLink connections have only been supported to a primary disk system has been a detractor from using zHyperLink in some environments that benefit from HyperSwap.
To improve on this, IBM is introducing “Consistent Read from Secondary” code. This code, among other things, adds a heartbeat to the Metro Mirror code. This allows the DS8000 to communicate to the z that everything is fully duplex and that it’s safe to issue a read to the secondary. It also allows the IBM z systems to detect the latency, over FICON or zHyperLink, and determine which system will offer better read performance.
As a result, if, for example, a HyperSwap were issued and moved the Primary DS8900F system to another part of the data center, the secondary may now be the closest one. Those workloads that use the Media Manager I/O driver (zHyperLink eligible reads from Db2, VSAM, and IMS), would use the secondary disk system instead.
This also has significant benefits where there might be multiple IBM z systems that are both using the same primary storage, but the Metro Mirror secondary is closer to one of them. In that case, that IBM z system could issue reads to the secondary DS8900F system while doing writes to the Metro Mirror Primary.
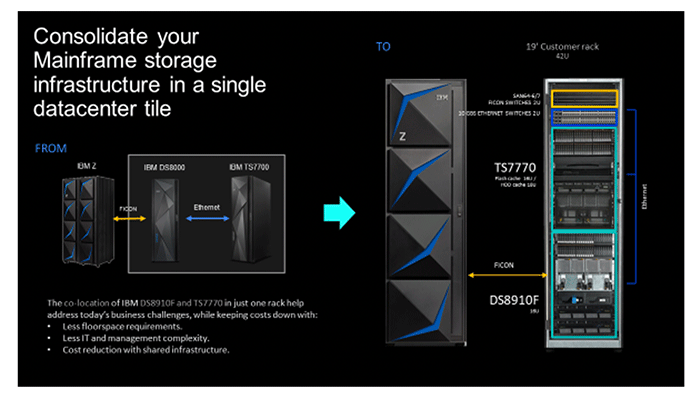
- Mainframe Infrastructure Consolidation
As customers begin to do more work in colocation facilities, IBM has worked hard to shrink the footprint of the IBM z systems (including IBM LinuxOne for customers who wish to consolidate their Linux server infrastructure), the DS8900F systems, and the TS7700 Virtual Tape Libraries. This has led to all of them fitting into standard 19″ racks and losing so much of the bulk that defined them in earlier generations.
Summary
The new announcements for the DS8900F family show that IBM’s flagship disk system is continuing to innovate. With enhancements to Safeguarded Copy, customers will get enhanced protection from the growing threat of Ransomware, and the new DS8980 will provide the highest levels of performance for the most demanding AI and ML workloads.
If you have any questions about this new system or the new capabilities in R 9.2 (including several in addition to what was listed here), reach out to your Mainline Account Executive directly or contact us
here.
You may be interested in:

