Today’s computing environments are facing ever-increasing cyber threats with greater severity and cost than ever before. Cyberattacks by ransomware or malware are ever changing and can have significant impact on service delivery, hinder the ability to provide goods and services, impede business continuity, damage the corporate reputation, and cause severe financial loss and expense both from the attack(s) and recovery from the attack(s).
Historically, IT environments initially focused solely on in-house backup, then came off-site storage, then came Disaster Recovery facilities. Today’s environment now requires a cyber-resilience strategy. That strategy should include several key components:
That strategy should include several key components:
- Identification
- Protection
- Detection
- Incident Response
- Recovery
The IBM z Cyber Vault (IzCV) is an architectural infrastructure leveraging IBM software, hardware, and services to deliver world-class cyber resilience, intrusion detection, data recovery, and data corruption protection from internal and external threats. The solution provides protection from logical data corruption, trusted data sources via validation and verification, confidence for IT staff to restore the business, and a uniform, dependable infrastructure for applications and tooling.
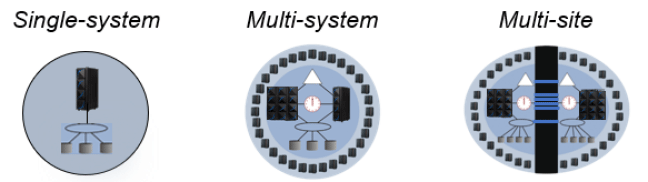
Whether an organization has a single-system, multi-system, or multi-site zOS implementation, IzCV can be established and implemented to provide a high level of cyber-resilience.
Components of an IBM Z Cyber Vault Solution
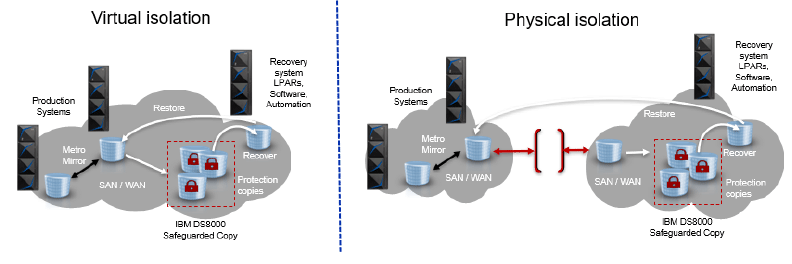
IBM hardware and software components for an IBM Z Cyber Vault solution include the following:
- IBM Z hardware (zOS-based) w/isolated LPAR
- IBM DS8000 Storage with Safeguarded Copy
- IBM Software products for data validation, forensic analysis, and surgical recovery
- IBM Geographically Dispersed Parallel Sysplex (GDPS) or IBM Copy Services Manager (CSM)
- IBM System Recovery Boost (faster recovery time for IBM z15+ processors)
Reference Architecture
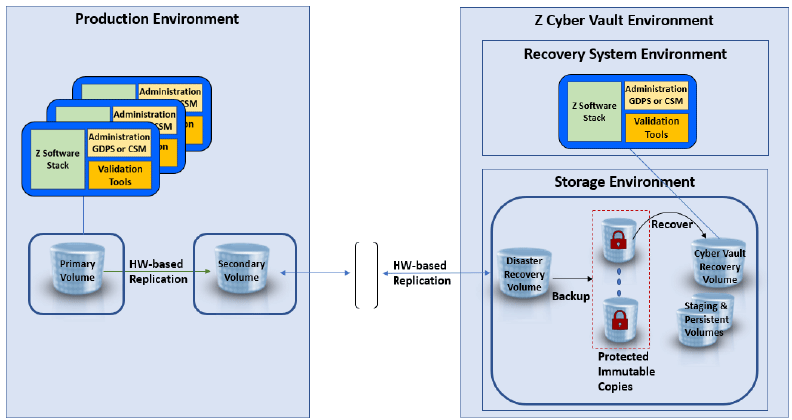
The reference architecture for the IBM Z Cyber Vault solution requires two separate domains: the existing production environment and an isolated Cyber Vault environment. The Cyber Vault environment consists of both a storage environment and a recovery environment. The storage environment is composed of DS8000 storage with either Copy Services or Safeguarded Copy.
The recovery environment contains all the software from the production environment, including tooling for data validation, forensic analysis, and recovery. The recovery environment is typically started from a “point-in-time” data image of production, keeping the environment isolated with limited user access. Validation, testing and forensic analysis can then be performed within this recovery environment. Various automations are available to run the data validation tasks as fast and error-free as possible.
Other variations of the reference architecture are leveraged relative to whether the environment is single-system, multi-system or multi-site. IBM Z Cyber Vault can leverage technologies like GDPS Metro and GDPS Global implementations.
Summary
The IBM Z Cyber Vault delivers cyber resiliency protections for customers to identify data corruption, protect data assets, and enable rapid recovery from a cyber incursion. IzCV is designed to complement existing high-availability disaster recovery solutions and the existing infrastructure.
More Information
As an IBM Platinum Business Partner, Mainline has extensive experience with IBM systems, including IBM Z mainframe systems and operating systems (z/OS, z/VM, z/VSE, and Linux), enterprise storage and data protection platforms, and cybersecurity solutions. Mainline’s enterprise specialists can help you analyze, architect, and implement a cyber resiliency solution to protect your data assets and enable rapid recovery actions from a cyber incident or attack. To set up an in-depth discussion, please contact your Mainline Account Executive directly or click here to contact us with any questions.
You may be interested in:
Blog: Cybersecurity in 2022 – 5 Priorities for Business Leaders
Blog: Securing Any Data, Anytime from Everyone with IBM Z
OnDemand Video: IBM Z Cyber Resilience and Business Continuity (39:41)

