It’s mid-2021 and it looks like the fog of the pandemic is starting to lift. While I would like to say that things are going to return to the old business as usual, nothing could be further from the truth.
The crisis has permanently altered the way that many companies operate. Organizations have been forced to embrace technology to support digital activities such as Work from Home/Work from Anywhere, that they traditionally felt would harm productivity. Much to their surprise, these new work environment practices have instead delivered huge gains in productivity and a reduction in operational costs.
As much as I’d love to further address these “unforeseen” advantages in terms of economics and productivity, that is the subject for another time. The focus of this post will be on a particular set of solutions that enable organizations to adapt their stopgap solution into a new remote workforce strategy that supports digital transformation.
Identity and Access Management (IAM)
Instead of accelerating plans to bring people back to the office, we are seeing businesses double-down on cloud services and efforts to strengthen security for their remote workers. For many, this means getting a new VPN/SASE or VDI solution in place, but we usually also arrive at a discussion around IAM solutions.
There are many reasons, but if we boil it down to its simplest form – organizations need to know who the authorized users are in their environment, what they can access, and keep track of what they are doing while they are there.
This may sound simple in theory, but in practice, this has traditionally been one of the most complicated and frustrating endeavors because it’s a problem that scales with every system or application that is added to the environment.
- A common example – When a company adds a new-hire, it can often take weeks to provision the proper access to networks and/or applications.
Times are changing though. Technology has improved and organizations are committed to adopting solutions to streamline user administration, enhance security controls, and simplify the end-user experience.
- Single Sign-On (SSO), Multi-Factor Authentication (MFA), Privileged Access Management (PAM), Risk-Based Authentication (RBA), or Governance Risk and Compliance platforms (GRC) – these are all great examples of secure access solutions our clients are looking to implement, and they are finding that leveraging the Cloud is the best way to bring it all together!
The World of Cloud Identity
I’ve been working with Identity solutions for years, and I can’t tell you how many times a project has gotten shelved due to a lack of resources for the integration efforts or concerns over availability. But cloud solutions have completely changed this paradigm.
Cloud Identity platforms are leveraging open standards and have templates for integration into all the common, and sometimes not-so common systems. These platforms are always available, no matter where your users are located or from what device they are connecting.
Common features to expect from these solutions:
- Secure Single Sign-On access to sanctioned applications from anywhere
- A common MFA that you can leverage across all your devices, applications, and services
- Password-less authentication
- Control and even record the sessions your admins or contractors have when they escalate privileges
- Conditional Access so you can dynamically limit a user’s access based on risk characteristics
- Powerful automation features like – Provisioning/Deprovisioning user accounts directly from your HR suite
- Workflows that integrate with your ticketing system and can empower your managers with the ability to approve or deny access on request
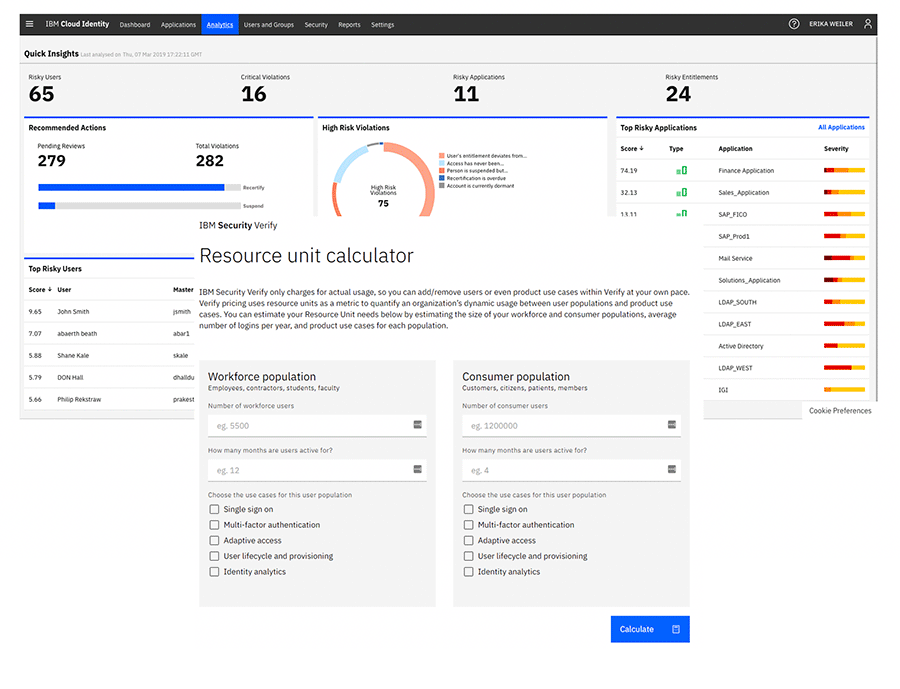
- Entitlement reports for your auditors that are available anytime
- Extending these controls to your partners & consumers when they access your site
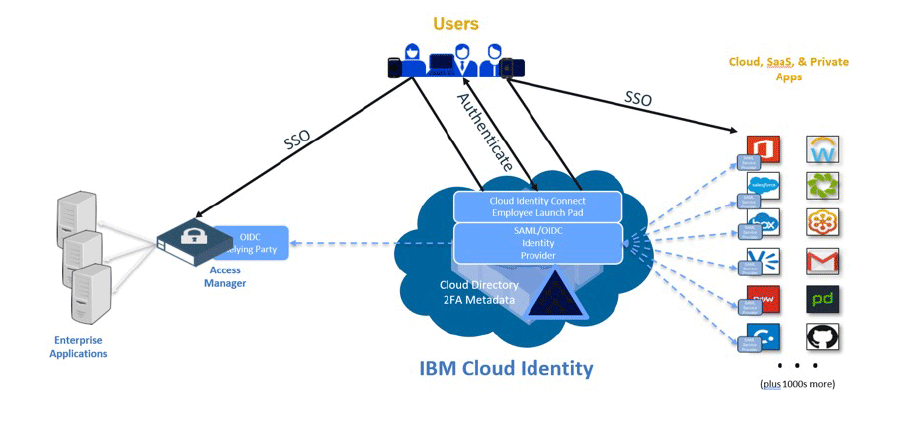
Meet IBM Verify Suite
An industry benchmark in IAM, IBM has been a top-ranked solution for decades. Over the last 10 years, IBM has transitioned from the traditional on-premises solution for which they’ve been known, to a full-featured Cloud Identity stack that rivals anything else available in the security marketplace. IBM Verify Suite can be deployed however you need it – on premises, in the Cloud, or in a “hybrid” mode (Hybrid Cloud).
Mainline Security Practice – Making Security Easier
Choosing the right Identity solutions for your company can be a challenge, but Mainline can help make that easier for you. Whether it’s a transition to Cloud or trying to optimize your Work-From-Home strategy, Mainline has experienced resources that can understand your requirements and guide you through selecting the optimal solution. From analyzing the current architecture to designing and implementing a new solution, Mainline has the proficiencies necessary to put your environment on secure footing. For more information on security solutions, reach out to your Mainline representative directly, or click here with any questions.
You may be interested in:
BLOG: Cybersecurity in a Remote Work-From-Home World
BLOG: Best Practices for Encryption Key Management
BLOG: Using IBM Cloud Pak for Security to Help Your Security Teams Address Risk

