Systems Engineer – Storage Solutions
During 2021, a cyber-attack is expected to occur every 11 seconds.1 The results of a 2021 global study found that data breaches now cost businesses an average of $4.24 million, up from $3.86 million in 2020, or upwards of a 10% increase.2 That’s quite a looming threat over everyone’s heads and if you’re not prepared this can be devastating to your corporation.
Cybersecurity and data protection have never been more paramount. There are 4 key pieces to data protection which I like to think of as a layered approach:
- Replication – Whether you have two or three sites, HyperSwap, metro mirror, global mirror or metro-global mirror, on premises or in the cloud, replication protects against localized disasters. My coworker and Mainline Systems Engineer, Ian Wright, has a blog on the topic that is found here.
- Encryption: Protecting your data from prying eyes, complying with regulations, and assuring yourself that in the event of a physical relocation or even sending bad drives back to the manufacturer, your data can’t be accessed. With IBM FlashSystems running IBM Spectrum Virtualize, this can be done with either USB keys or using IBM Security Guardium Key Lifecycle Manager(GKLM), formerly known as SKLM. Matt Likes, Mainline Security Architect, has a blog on encryption here.
- High availability: Having immediate access to your data in the event of an issue. Maybe an upgrade went horribly wrong or maybe a rack in your datacenter lost power; with IBM’s HyperSwap you have dual-site active-active access to a volume for high availability.
My vlog on high availability is found here. - Immutable copy: Creating a copy that is logically or physically air-gapped from the primary volume. This means the host cannot address the volumes and they are unchangeable in the event your primary data is compromised. This is the topic of today’s blog.
A part of the IBM Spectrum Virtualize code update 8.4.2 being released on August 27, 2021, Safeguarded Copy on IBM FlashSystem makes its debut. IBM Safeguarded Copy is a virtual airgap mechanism that uses FlashCopy functionality to take immutable snapshots, aiding in the recovery from ransomware or internal ‘bad actors’ who would seek to destroy data.3 It creates point in time copies of data that can’t be changed by error, malicious destruction, or ransomware attacks. Within this feature there are three key components: Separation of Duties, Protected Copies, and Automation. Let’s dive into each of these further.
1. Separation of Duties
Roles currently available in Spectrum Virtualize from least (left) to most (right) authority/access:
Monitor » Copy Operator » Restricted Administrator » Administrator » Security Admin » Superuser
To boil down what this means for Safeguarded copy, if the Administrator cannot remove a Safeguarded Copy, then neither can the restricted administrator, copy operator or monitor. Administrator role and below are restricted, they are used for day-to-day tasks. They can configure Safeguarded Copy but cannot remove them. They can look but they can’t touch. They cannot remove the Safeguarded (backup location) child pool either. They also cannot delete the original volume if it has Safeguarded Copies associated with it. Modified Safeguarded Policies only apply to new backups and the original backups retain the policy with which they were created. Superuser handles the most sensitive maintenance and has the highest “clearance” level in the system. They can delete Safeguarded Copies and Safeguarded Child Pools. If you’re still concerned with this, you can not define any Security Admin user and disable superuser, but if you need support to perform advanced tasks then you must reenable them via physical access to the array or through IBM Remote Support.
2. Protected copies
Based on existing technology within Spectrum Virtualize, Safeguarded copy borrows FlashCopy snapshots. It’s a thin-provisioned point-in-time copy of production volumes and utilizes Child Pool technology for a logical separation from other volumes. This segregation allows for capacity controls and access restrictions.
3. Automation
IBM Copy Services Manager (CSM) is required to manage, implement, and schedule Safeguarded Copy for IBM Spectrum Virtualize. It is also required for the DS8000 version we already know and love. CSM is external software that runs on a VM or x86 server. It tells Spectrum Virtualize when to make copies and how long to keep them. CSM doesn’t do any of the heavy lifting: Spectrum Virtualize handles the deletion of expired backups internally. It can coordinate and catalog copies across multiple clusters so to easily manage your complex environment. CSM allows you to automate, manage, and restore your Safeguarded Copies with either IBM provided policies or ones you create yourself using the CLI. As a side note, policies can only be deleted if they have no volume group associated with them.
Use Cases
Data recovery and restoration can span from more minor, or contained, situations to catastrophic. Safeguarded Copy can be utilized across the recovery range. Here are some use cases:
- Validation – Since you can’t directly address or mount the Safeguarded copies, you’ll have to recover the copy to another volume/LUN and map it to a host. Make sure as part of your regular test plans you include Safeguarded copy to validate your data. Analytics can help with early detection of a problem or reassurance that your copy is pristine. Once you know the correct copy to restore, data can be restored to production.
- Forensic – In most cases, I recommend restoring to a new volume instead of overwriting the original production source so that you can still perform forensic investigation on the original data.
- Surgical – You can extract data from the copy to restore back to the production environment. One application may have only been affected compared to the whole system.
- Catastrophic – In the event of a catastrophic issue, you can recover the entire environment back to a point in time from your Safeguarded copies. Take these for anything you may want to recover but be aware of space and copy limitations.
- Offline Backup – You can perform an offline backup that can be used as a secondary line of defense providing more security and greater retention. IBM Spectrum Protect is ideal for this use case.
Planning for Safeguarded Copy
Cache is king, but when in doubt go with a higher cache on the system, otherwise you’ll need to consider the performance and overhead of extensive numbers of FlashCopies (and this is also why it’s not available on ALL arrays running Spectrum Virtualize).
- Additional Space required for Safeguarded Copy depends on three factors:
- Volume capacity (number of volumes and size)
- Data change rate
- Number of daily snapshots
- Guidance for configurations will be available in the STorM tool
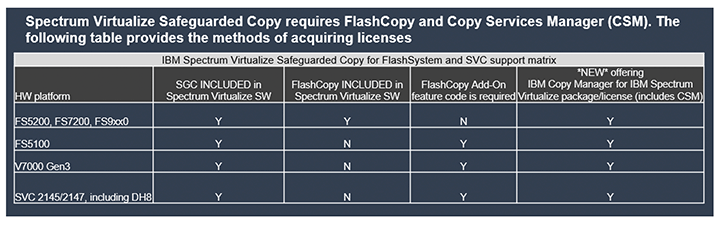
- Copy Services Manager can be licensed in numerous ways. Your Mainline representative can help you configure the most cost effective solution for your environment.
Difference between IBM DS8000 and FlashSystem Safeguarded Copy
The IBM DS8000 supports both mainframe (FICON) and Fibre Channel environments, but the primary use and growth for DS8K has been in the mainframe world. 4 Nonetheless, Safeguarded Copy is on both the FlashSystem and the DS8K and there are significant differences. You can check out my vlog on DS8000 Safeguarded copy, but here’s a brief rundown comparison:
Both versions have immutability, separation of duties, non-accessibility by hosts, utilize CSM for scheduling/testing/recovering, and can restore directly to production. (On the DS8K this happens at release 9.2.)
The differences lay in implementation details:
- With the FlashSystem Safeguarded Copy, you get pre-defined policies from the GUI, while on the DS8K you must create your own.
- You can have up to 32 policies on the FlashSystem but you’re free of those limits on the DS8K.
- Initiating the CSM relationship is done on the Spectrum Virtualize side with FlashSystem but it is done by a CSM administrator on the DS8K.
- Backup capacity is defined for each FlashSystem Safeguarded Copy location (or child pool) but on the DS8K it’s defined for each volume.
- The FlashSystem supports 256 Safeguarded copies per source volume, but the DS8K tolerates 500 copies per volume.
Workflows
10 minutes and you’re up and running (as long as you’ve already updated your code).
I can sense your disbelief through the internet, so here are the two workflows:
1. Spectrum Virtualize workflow
- Create Administrator user for IBM Copy Services Manager
- Create Safeguarded backup locations (child pool)
- Create volume groups and add source volumes
- Assign Safeguarded backup policies to volume groups
2. Copy Services Manager workflow
- Create the Administrator user
- Create a connection to the system in IBM Copy Services Manager
- After a connection is established, IBM Copy Services Manager automatically detects volume groups with Safeguarded backup policies and schedules the backup copies
- Optional – setup Dual authentication control
Caveats
Yes, there are always some caveats. Here’s the fine print:
- Safeguarded copy supports a maximum of:
- 256 volume groups
- 512 volumes per volume group
- 256 safeguarded copies per source volume
- 32 Safeguarded policies
- 3 default IBM supplied policies
- Source volume of a Safeguarded copy cannot be:
- A mirrored copy of a volume
- In an ownership group
- A change volume that is used in either HyperSwap or Global Mirror relationships
- Used as cloud backups with the Transparent Cloud Tiering (TCT) function
- Spectrum Virtualize for Public Cloud (SV4PC) is not currently supported by Safeguarded Copy
- Safeguarded Copy is not supported on these specific models – V50X0E, FS50x0, FS50x5, V7000G2/G2+. The required code level for Safeguarded Copy is 8.4.2 and up
- Safeguarded Copy does NOT replace offline backups.
Integration with IBM Security QRadar for Security Monitoring
Some ransomware attacks take up to 200 days to be found, but not to worry. Talk to your Mainline rep about complimentary IBM tools, such as QRadar, to help detect a cyberattack early. IBM QRadar analyzes event data in real time for early detection of attacks or breaches. It includes real-time alerting on potential threats and integrates to trigger Safeguarded Copy based on abnormal login attempts such as from an unusual IP address, outside normal working hours, or multiple failed login attempts.
Next Steps
If you have a legacy IBM storage SVC, V series, or FlashSystem arrays running Spectrum Virtualize, Safeguarded Copy is the next step in your data protection scheme. Allowing for granularity of immutable point-in-time copies, restricted access, and automation, don’t delay in planning to take advantage of the new technology.
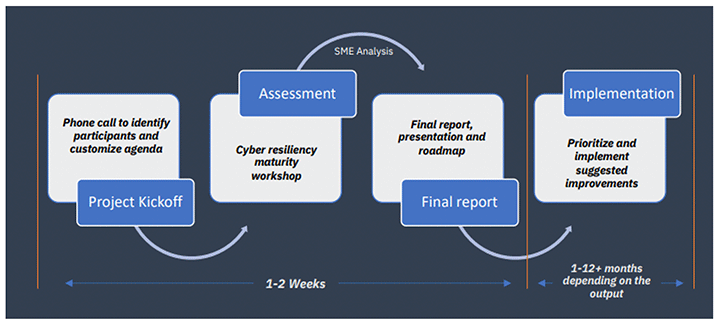
If you’re looking for more help/suggestions to make your storage systems more resilient, ask your Mainline representative about the IBM Cyber Resilience Assessment. Completely funded by IBM, it’s a 2-hour virtual workshop that includes a detailed final report and roadmap of recommended improvements based on the NIST Security Framework and the Storage Cyber Resiliency Assessment Tool (CRAT). The assessment evaluates your current data protection state, identifies gaps, strengths, and weaknesses, and provides recommendations.
More information
Reach out to your local Mainline Account Executive, or contact us for help with crafting a cyber resilience strategy for your business and how learn more about integrating Safeguarded Copy into your environment today. With 30+ years of experience in enterprise IT solutions, we’ll find the best solution for your business needs and strategy.
Related articles
BLOG: IBM Spectrum Virtualize Continuous Availability and Three-Site Replication
BLOG: Best Practices for Encryption Key Management
VLOG: IBM-Storwize-Functionality
VLOG: IBM DS8880 SafeGuarded Copy
BLOG: IBM DS8000 – The Market Leader for Mainframe Storage
Footnotes:
2Cost of a Data Breach Report, conducted by Ponemon Institute and sponsored and analyzed by IBM Security
3IBM Storage Safeguarded Copy Field Training Guide
4Mainline Information Systems, Blog: IBM DS8000 – The Market Leader for Mainframe Storage

