There’s been an awful lot of buzz around Zero Trust (ZT) these days. Many of our customers ask us, “What is ZT?”, “Do I need a ZT Architecture?”, and “How do I implement Zero Trust?” This IBM infographic illustrates some eye-opening statistics of today’s reality characterized by evolving threats, changing variables, and unknowns, that certainly suggests the absolute need for ZT.
If you are being tasked with building a Zero Trust Architecture (ZTA) or if you’re simply interested in learning what it’s all about, a ZT workshop is a great way to get started. But more on that later.
Let’s talk about ZT.
Will the Real Zero Trust please stand up?
From asset management solutions to Cloud IDPs, solutions are popping up all over the industry that claim to be THE enabler for your Zero Trust Architecture. But what does this really mean? Are all these solutions doing something new? Are they essential to the success of ZT?
While there is a grain of truth to the claims of these solutions, many of them are relabeling their solution so that they can take advantage of the hype. I’ll give you a quick analogy: It’s akin to milk companies slapping a “gluten-free” label on their carton – Newsflash – Milk has always been gluten free!
That said – systems that businesses have been using for years are often already capable of plugging into a Zero Trust Architecture. The real question is if the right pieces are in place to produce a legitimate ZTA.
Let’s unpack this…
First, what is Zero Trust?
At its core, Zero Trust is a design philosophy that assumes the inevitability of unauthorized attempts to access and potentially exploit systems and apps.
In practice, it suggests:
1. The removal of implicit trust at every level of the stack
2. Only granting entitlements according to granular policies
3. Authorizing access based on a high degree of certainty that all entities involved in a “transaction” are in fact who they say they are.
4. Monitoring usage patterns for future decision making
What does a Zero Trust Architecture look like?
The answer to this question will depend greatly on the details of an environment, but I’ll provide some examples of the typical components and the roles they play in ZTA.
NOTE: This is nowhere close to a complete list, but they frequently come up in our ZT workshops.
Sources of Truth
This is the beating heart of any ZTA. Like the name implies… These should be highly credible data sources that provide essential information about your environment to your security controls. Some excellent examples are:
» Identity & Access Management (IAM, IDaaS)
Identity is at the core of ZT, so this is a must-have
» Microsoft Active Directory is common, but we’re seeing more and more organizations that are putting their trust in Cloud solutions like IBM Verify that have native plugins for SaaS applications as well as traditional applications.
» IT Asset Management (ITAM), Change Management (CMDB), IP Address Management (IPAM)
You can’t protect it if you don’t know it exists.
» Much like Identity, where you are managing authorized “users”, these tools help in understanding authorized devices and applications. They provide valuable intelligence that can aid in weeding out or possibly even preventing false positives identified by your Security Controls.
Common Controls for ZT
These are the eyes, ears, and hands for ZT, and they are responsible for enforcing policy.
» Multifactor Authentication
These work tightly with your IAM and are a critical element for ZT. We specifically recommend solutions that provide an “Adaptive MFA” like IBM’s Verify Suite. These products make “smart” decisions about what type of challenge a user should see. They gather intelligence and pass a “confidence score” to other controls within the environment.
» Privileged Access Management
These manage/monitor/broker escalated privileges on your devices. These solutions can prevent Ransomware from ever getting close to your prized assets by controlling the “who, how and when” root/admin privileges can be used. I’d urge you to see a demo of IBM Verify Privilege.
» Network Behavioral & Anomaly Detection
Encompassing a broad range of products – These solutions are a key piece in understanding user traffic within an environment. Systems like IBM QRadar leverage this data to identify risky user/process traffic and report it back to your SOC. There is a bit of overlap here with NGFW/IDS/IPS, but those devices are a bit special in that they not only spot risky traffic but can also shut it down based on policy.
» Secure Access Service Edge (SASE)
This technology is quickly becoming the replacement for legacy VPN solutions. They combine Secure Remote Access, Content Filtering, and Cloud Access Security Brokering (CASB). They not only establish secure connections to enterprise assets, but they also provide control on how/if an endpoint connects to various Internet sites & Cloud services.
» Network Access Controller (NAC)
Simply put – If a user/system can’t authenticate, it has no business being on your network. These solutions allow you to control how/if a user or process can even communicate on your internal network. They can dynamically configure routes for VLAN traffic based on user/process/device segmentation policies and enforce posture assessments. Truly a must-have.
» Data Access Monitoring
Covering a broad spectrum here – These solutions can include your Data Discovery/Classification DLP, DAM, FIM/FAM tools of the world. These solutions specialize in monitoring how users are accessing data.
» Unified Endpoint Manager and/or Endpoint Detection & Response
It doesn’t get any more frontline than these tools. They run on the endpoints and are used to perform ongoing posture assessments, maintain hygiene, and can enforce policy to prevent unauthorized activity in host processes.
Putting it all together:
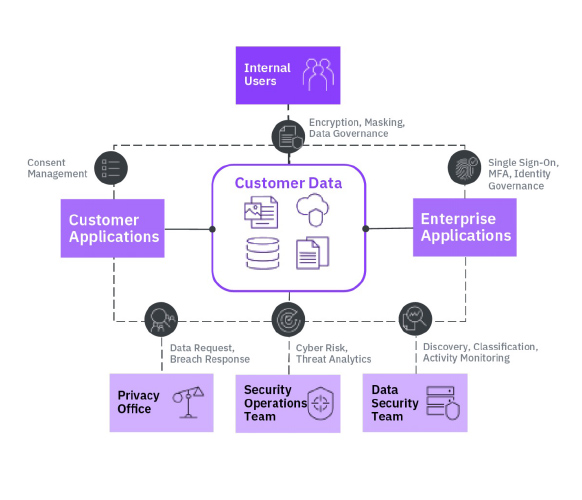
In a properly integrated ZTA, your controls can identify any user logging in from any device in the world and dynamically control their access to any asset based on the level of confidence.
As time goes on… usage patterns emerge, and your access controls will become even better at making decisions on their own.
Your IA & PO will be able to pull reports on exactly who had access to what and when, and your SOC team can leverage this same data for threat hunting efforts.
ZT Workshops
ZT Workshops are engagements designed to help you get a better picture of ZT elements you may already own and to understand what gaps may exist, saving you months of research (and headaches). Depending on the complexity of the environment, a ZT Workshop can take as little as 4 hours or can be multi-day. Mainline certified professionals perform these workshops at no cost, and we talk technology, not product. We offer both on-site and remote workshop options.
More Information
Mainline offers a comprehensive portfolio of security, governance, and risk mitigation solutions. If you’re interested in learning more about Zero Trust models, in scheduling a ZT Workshop to help you design your own ZT, and/or assistance in implementing a Zero Trust approach, contact your Mainline Account Executive directly or click here with any questions.
You may be interested in:
BLOG: Cybersecurity in a Remote Work-From-Home World
BLOG: Security Challenges in a Multi-Cloud Environment
BLOG: Using IBM Cloud Pak for Security to Help Your Security Teams Address Risk

